90% of our clients receive immediately actionable NIS-2 solutions
What is NIS-2? The Essential Facts (2025)
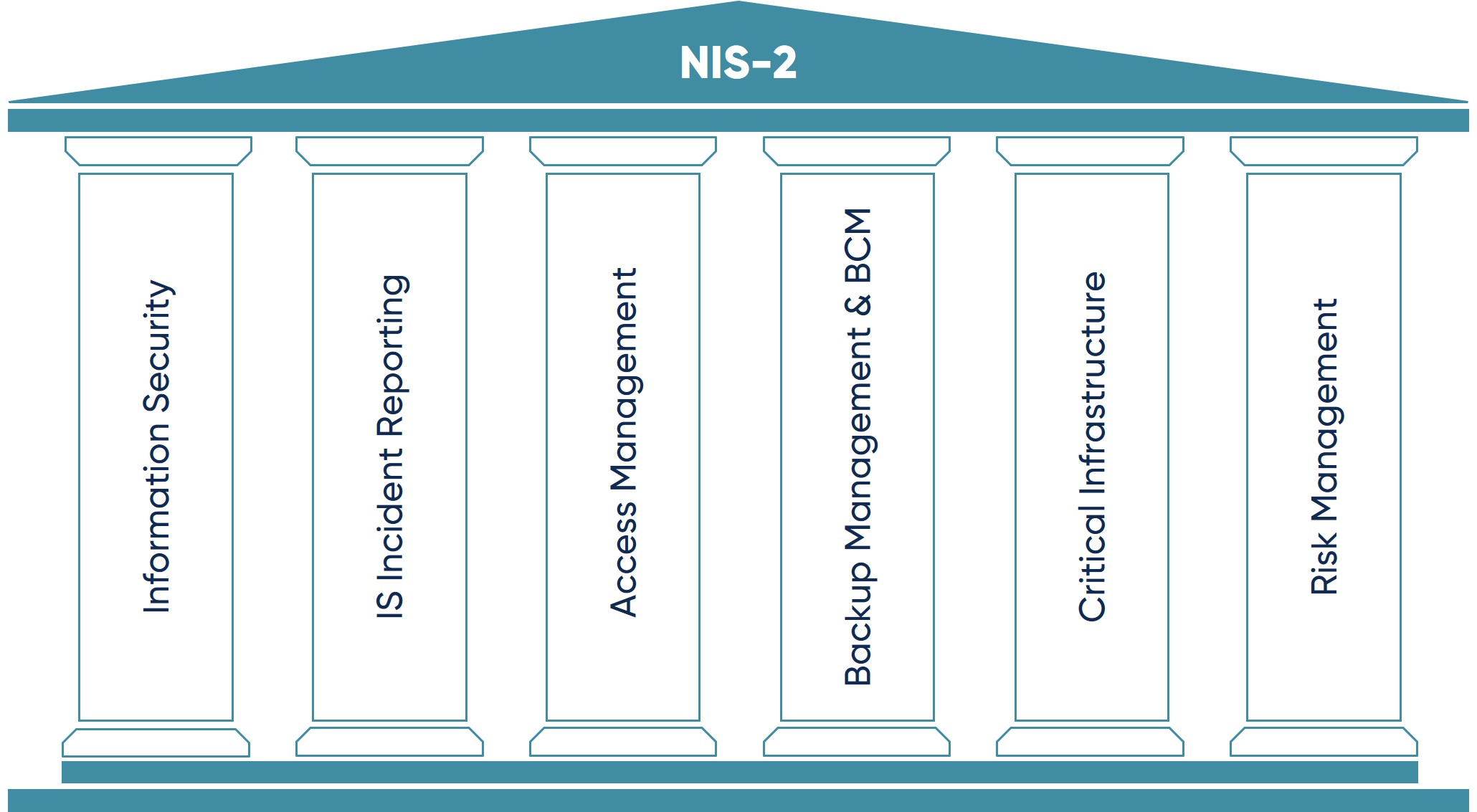
The NIS-2 Directive affects approximately 29,000 UK companies across 18 sectors since October 2024. Companies with 50+ employees or €10+ million turnover must register with national authorities and meet cybersecurity minimum standards.
Quick Check: Energy, transport, banking, healthcare, manufacturing, telecommunications affected?



![[Translate to English:]](/fileadmin/_processed_/2/a/csm_2024-04-19-PORTRAET-Friedich-Jochen_939a81a19c.jpg)
![[Translate to English:]](/fileadmin/_processed_/d/9/csm_2022-07-12-PORTRAET-Dusch-Tobias_d2e43c7ddc.jpg)

